TCT is committed to helping you keep your organization secure and compliant. Every quarter, we publish compliance and security insights that you can share with your employees to fulfill periodic security reminder requirements your organization may be subject to.
As an added bonus, we’ve highlighted some developing security trends and featured a quick tip to get more out of your compliance management.
Inventory Best Practices
PCI DSS requires you to inventory your devices. No problem, just put a list of devices together and you’re done. Bada boom, bada bing. Sounds simple, right? Not so fast. Chances are, your device inventory doesn’t make the grade — even if you believe you’ve done it right.
Often, when I engage with clients, I see a half-hearted effort to put a list of stuff together and call their inventory done. Most inventories look like a random hodge-podge of workstations and servers. It’s not that these organizations didn’t care — they just didn’t understand the purpose of the device inventory within PCI DSS and what it’s used for.
Don’t Forget About These Important Device Policies
Why Your Device Inventory Matters
Device inventories become a lot clearer when you understand what they’re for and how they’re used. So before you begin compiling your list of devices, I recommend taking a step back from the inventory and asking, “Why is it that we need to have this list of stuff in the first place? Who cares?”
Every requirement in PCI DSS includes elements that depend on having a device inventory, so that you can be sure nothing slips through the cracks anywhere within your entire organization. The inventory is your accounting of every device and piece of software that needs to comply with all of the various PCI DSS controls.
As you’re going through PCI’s list of controls, you should ask yourself, “How will I track each device that’s subject to this control?” The answer: your device inventory!
It’s surprising how often you’ll need to refer to your device inventory, even when you aren’t managing PCI DSS. For example, if there’s an attack on a particular piece of technology, you need to know everything else that could be impacted. How do you easily identify it all? Check the inventory. Maybe there’s a new critical patch for a certain system. Where do you need to apply it? Check the inventory. How do you validate that your antivirus is updated on all the appropriate systems? Compare the list of covered systems to the inventory.
Scoping Your Device Inventory
PCI only requires you to include the devices that are within the scope of your compliant environment. However, at TCT, we strongly recommend that you include every device that has an IP address externally or internally. At the end of the day, you don’t simply want to be compliant — you want to be protected.
Include all of your environments. There’s a lot of discussion in PCI DSS about the scoped environment. Most people limit that to the production environment, especially in a code-based organization. But they won’t put the same level of detail into the environments like their headquarters, sales offices and remote personnel. That’s a mistake, because any environment with an internet connection needs to be tracked and managed.
Include all relevant workstations. It’s easy to miss random workstations, especially if your company has remote employees or multiple locations scattered across time zones. Be sure nothing slips through the cracks.
It isn’t just environments and workstations that need to be included in the device inventory. There’s a ton of device categories that people frequently overlook, simply because they don’t think of those devices as relevant — or even as devices.
For example, your device inventory should include anything that’s your responsibility or that exists on network segments that draw IP addresses within your control. That can include things like cameras, printers, badge access panels, wireless access points, smart TVs, and work-issued mobile devices.
Change Control
Your device inventory is a vital part of your change control process. It helps you easily deploy new assets, modify existing assets, and deprecate old ones. Update your inventory as you make these changes. It should be built into your change management process, so that the modifications are made immediately to the inventory and the updates are quick and easy to do.
Software Considerations
Your inventory shouldn’t be limited to physical devices. Include software on your inventory as well. Often, an organization only includes the software applications at the core of their operations. The inventory is intended for all of your software, because attackers don’t care if a vulnerability lies in a humongous software system or a tiny application. They’ll use any means possible to get into your network.
Look at everything that’s installed on your systems across your entire environment. Don’t forget firmware. Also don’t forget third-party software components that your company uses to build your own software — including browser add-ons. Look a level deeper than your web server — look at the web code as well, to determine all of the third-party components.
Why include software in the device inventory? Consider patching. How can you be sure all of your software applications have the latest patches unless you’re able to track everything within your organization? The inventory helps ensure you’re cognizant of the fact that there are patches for your software.
Another benefit of maintaining a software inventory: you’ll discover all of the rogue applications that you never knew had been installed on employees’ devices. You’ll also discover who has the ability to install applications but shouldn’t have it. Maintaining your software inventory is a great way to fix permissions levels throughout your organization.
TCT Portal Quick Tip: Repeat What Worked Last Year
Every single year, without fail — even if everyone on your team has been around for years — you can guarantee that people will need reminders about how to fulfill certain compliance assignments.
- How is this supposed to be done again?
- What evidence was provided for that requirement?
- What additional explanations need to be included for this item?
Many months have passed since the last time various tasks were completed, and team members will have questions about fulfilling their assignments. If you have someone new on the team, they won’t have a clue how to do various tasks, or what the Assessor requires.
You can avoid the constant barrage of questions and handholding by taking advantage of TCT Portal’s capability to reference the Explanations and Attachments from your prior certification track.
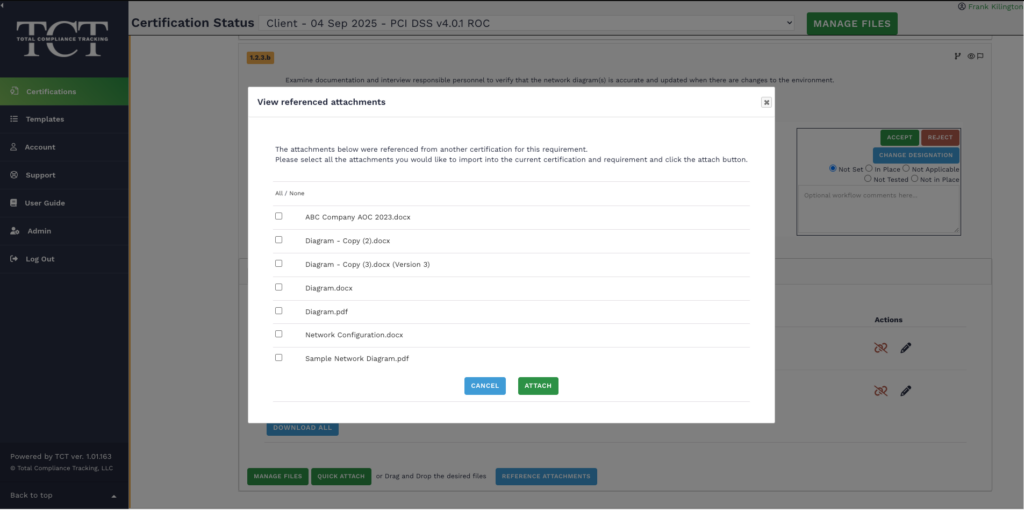
You’ll be able to refer to the previous year’s explanations and attachments. You’ll have the ability to attach them to your current track directly from within TCT Portal — no need to hunt evidence down on your storage systems or recreate screenshots. You can even make modifications to files from the prior track, as needed.
It’s easy to start referencing prior evidence. As long as you have evidence from a prior track in TCT Portal, simply submit a request to the Portal Support Team to turn on the ability to reference prior explanations and attachments.
Save a ton of time on the engagement, allow your team to operate independently, and get new team members onboarded fast. Best of all, you’ll have greater confidence that your Assessor will approve your evidence the first time it’s submitted.
What’s Going on in Security Today
Hacker Charged With Seeking to Kill Using Cyberattacks on Hospitals
Ahmed and Alaa Omer, of Anonymous Sudan, have been accused of using over 35,000 separate Distributed Denial of Service (DDOS) attacks against many targets. One of the charges is “seeking to cause physical death and injury.” The pair took devices in hospitals offline, some of which were administering life-saving treatments. This was tied to hacktivism activities for a profit. They declared on their telegram channel that the United States would be their primary target for the attacks. They also targeted systems in Denmark, Sweden, and India.
Exclusive: EU AI Act checker reveals Big Tech’s compliance pitfalls
Prominent AI models are falling short of European regulations in several important areas, like cybersecurity resilience. The AI Act is coming around in the next couple of years in Europe, and is intended as a way to put some guardrails around AI. Companies that fail to comply with the AI Act will face a 35 million Euro penalty when they spin up their AI instances.
DOJ Halts Major Russian Election Interference Plot Before 2024 Vote
The Department of Justice seized 32 internet domains that were part of a Russian government-sponsored foreign malign influence operation. These 32 domains were used by Russians to spread disinformation around the election coming up in November. Some of the tactics include cybersquatting, AI-generated content, fake social media profiles with inflated fake followings to push out propaganda. Other countries were also targeted, including Germany, Mexico, and Israel.
CISA Flags Critical SolarWinds Web Help Desk Bug for In-the-Wild Exploitation
The US cybersecurity agency CISA on Tuesday added a recent SolarWinds Web Help Desk (WHD) bug to its Known Exploited Vulnerabilities (KEV) catalog, warning of its in-the-wild exploitation. The flaw, tracked as CVE-2024-28987 (CVSS score of 9.1), is a hardcoded credential issue that allows remote, unauthenticated attackers to access internal WHD functionality and modify data.
TrickMo Banking Trojan Can Now Capture Android PINs and Unlock Patterns
TrickMo is an Android-based banking Trojan. In more recent variants, some new undocumented features have come to light regarding this malware. It has been discovered that TrickMo can steal a device’s unlock pattern or PIN to unlock the screen. TrickMo was officially discovered in the wild in 2019. With the new information found, attackers can access and use an infected device, even when the device is locked.
OnlyFans Hackers Disrobed by Malware in a Twist of Digital Irony
A notorious hacking forum, Bilalkahnicom, offered a tool for would-be attackers to “check” OnlyFans accounts. This tool basically turned predators into prey. In a twist of irony, the tool that was offered to criminals exposed the identity of the person leveraging the tool to go after OnlyFans accounts. The malware that performed the prey tracking was Lummac stealer.

Get industry insider expertise delivered to your inbox
Subscribe to the TCT blog

